What is SASE architecture? | Secure access service edge
Secure access service edge (SASE) architecture is an IT model that combines security and networking services on one cloud platform.
Learning Objectives
After reading this article you will be able to:
- Define the secure access service edge (SASE) model
- Learn about SASE architectural components
- Explore the benefits and use cases for SASE
- Understand how SASE relates to SSE and Zero Trust security
Related Content
Want to keep learning?
Subscribe to theNET, Cloudflare's monthly recap of the Internet's most popular insights!
Copy article link
What is SASE?
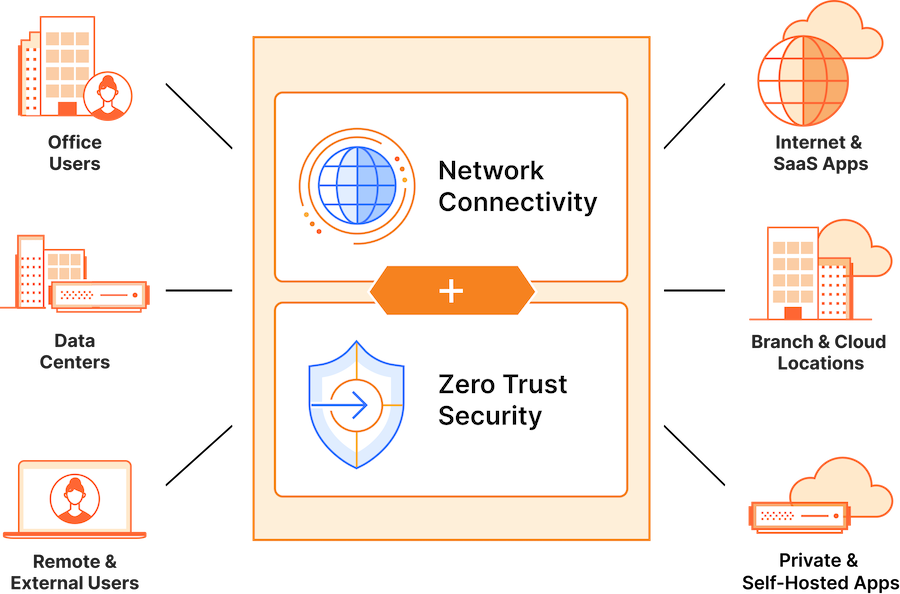
Secure access service edge, or SASE (pronounced “sassy”) is an architectural model that converges network connectivity with network security functions, and delivers them through a single cloud platform and/or centralized policy control.
As organizations increasingly migrate applications and data to the cloud, it has become more complex and risky to manage network security with a traditional “castle and moat” approach. Unlike the traditional networking approach, SASE unifies security and networking onto one cloud platform and one control plane for consistent visibility, controls, and experiences from any user to any application.
In this way, SASE creates a new unified corporate network based on cloud services run over the Internet — allowing organizations to transition away from many architectural layers and point solutions.
How does SASE compare to traditional networking?
In a traditional network model, data and applications live in a core data center. To access those resources, users, branch offices, and applications connect to the data center from within a localized private network or a secondary network (which typically connects to the primary one through a secure leased line or VPN).
However, this model is ill-equipped to handle the complexities introduced by new cloud-based services and the rise of distributed workforces. It is impractical, for example, to reroute all traffic through a centralized data center if an organization hosts SaaS applications and data in the cloud.
By contrast, SASE places network controls on the cloud edge — not the corporate data center. Instead of layering services that require separate configuration and management, SASE converges network and security services using one control plane. It implements identity-based, Zero Trust security policies on the edge network, which allows enterprises to expand network access to any remote user, branch office, device, or application.
What capabilities does SASE deliver?
SASE platforms combine network-as-a-service (NaaS) capabilities with a number of security functions managed from one interface and delivered from one control plane.
These services include:
- Network services that simplify connectivity, such as software-defined wide area networking (SD-WAN) or WAN-as-a-service (WANaaS), to connect a variety of networks together into a single corporate network
- Security services applied to traffic flowing in and out of the network to help secure user and device access, defend against threats, and protect sensitive data
- Operational services that provide platform-wide capabilities, such as network monitoring and logging
- A policy engine that underpins all contextual attributes and security rules, then applies those policies across all connected services
By merging these services into a unified architecture, SASE simplifies network infrastructure.
What are the technology components of a SASE platform?
Because secure access service edge involves converging a number of traditionally disparate services, organizations may move towards a SASE architecture progressively, instead of all at once. Organizations can first implement the components that fulfill their highest-priority use cases, before moving all networking and security services to a single platform.
SASE platforms typically include the following technology components:
- Zero Trust Network Access (ZTNA): The Zero Trust security model assumes threats are present both inside and outside a network; therefore, strict contextual verification is required every time a person, app, or device tries to access resources on a corporate network. Zero Trust Network Access (ZTNA) is the technology that makes the Zero Trust approach possible — it sets up one-to-one connections between users and the resources they need, and requires periodic reverification and recreation of those connections.
- Secure web gateway (SWG): A SWG prevents cyber threats and protects data by filtering unwanted web traffic content and blocking risky or unauthorized user behavior online. SWGs can be deployed anywhere, making them ideal for securing hybrid work.
- Cloud access security broker (CASB): Using the cloud and SaaS apps makes it harder to ensure that data stays private and secure. A CASB is one solution to this challenge: it provides data security controls over (and visibility into) an organization’s cloud-hosted services and applications.
- Software-defined WAN (SD-WAN) or WANaaS: In a SASE architecture, organizations adopt either SD-WAN or WAN-as-a-Service (WANaaS) to connect and scale operations (e.g., offices, retail stores, data centers) across large distances. SD-WAN and WANaaS use different approaches:
- SD-WAN technology uses software at enterprise sites and a centralized controller to overcome some of the limitations of traditional WAN architectures, simplifying operations and traffic steering decisions.
- WANaaS builds on the benefits of SD-WAN by taking a “light branch, heavy cloud” approach that deploys the minimum required hardware within physical locations and uses low-cost Internet connectivity to reach the nearest “service edge” location. This can reduce total costs, offer more integrated security, improve middle mile performance, and better serve cloud infrastructure.
- Next-generation firewall (NGFW) An NGFW inspects data on a deeper level than a traditional firewall. For instance, NGFWs can offer application awareness and control, intrusion prevention, and threat intelligence — which allows them to identify and block threats that may be hidden in normal-seeming traffic. NGFWs that can be deployed in the cloud are called cloud firewalls or firewall-as-a-service (FWaaS).
Depending on the vendor’s capabilities, SASE components above may also be bundled with cloud email security, web application and API protection (WAAP), DNS security, and/or security service edge (SSE) capabilities described further below.
What are the key benefits of SASE?
SASE offers several benefits compared to a traditional, data center-based network security model.
Reduced risk through Zero Trust principles: SASE leans heavily on the Zero Trust security model, which does not grant a user access to applications and data until their identity has been verified — even if they are already inside the perimeter of a private network. When establishing access policies, a SASE approach takes more than an entity's identity into account; it can also consider factors like geolocation, device posture, enterprise security standards, and a continuous evaluation of risk/trust.
Reduced costs through platform consolidation: SASE converges single-point security solutions into one cloud-based service, freeing enterprises to interact with fewer vendors and to spend less time, money, and internal resources trying to force disparate products to integrate.
Operational efficiency and agility: Instead of juggling point solutions that were not designed to work together, SASE enables organizations to set, adjust, and enforce security policies across all locations, users, devices, and applications from a single interface. IT teams can troubleshoot more effectively and spend less time resolving simple issues.
Improved user experience for hybrid work: Network routing optimizations can help determine the fastest network path based on network congestion and other factors. SASE helps reduce end user latency by securely routing traffic across a global edge network in which traffic is processed as close to the user as possible.
What are common SASE use cases?
Augmenting or replacing VPNs for modernized secure access
One common driver for moving to a SASE architecture is to improve resource access and connectivity. Routing and processing network traffic across a global cloud network as close to the user as possible — instead of through VPNs — reduces end user friction, while eliminating the risk of lateral movement.
Simplifying contractor (third-party) access
Secure access service edge extends secure access beyond internal employees to third-parties like contractors, partners, and other temporary or independent workers. With resource-based access, organizations mitigate the risk of overprovisioning contractors.
Threat defense for distributed offices and remote workers
SASE allows organizations to apply consistent IT security policies across all users, irrespective of their location. By filtering and inspecting all outgoing and incoming network traffic, SASE can help prevent threats such as malware-based attacks, multi-channel phishing (attacks that span multiple communication channels), insider threats, data exfiltration, and more.
Data protection for regulatory compliance
Because SASE provides visibility over every network request, organizations can apply policies to the data in each request. These policies help ensure compliance with data privacy laws that require organizations to process sensitive data in certain ways.
Simplify branch connectivity
A SASE architecture can help augment or replace a patchwork of multiprotocol label switching (MPLS) circuits and network appliances to more easily route traffic between branch offices, and to facilitate site-to-site connectivity across locations.
How are SASE and SSE (security service edge) different?
Industry analyst firm Gartner defines secure access service edge as including SD-WAN, SWG, CASB, NGFW, and ZTNA to “enable zero trust access based on the identity of the device or entity, combined with real-time context and security and compliance policies.”
In other words, SASE incorporates a user’s secure access as part of the network architecture. (It is worth noting here that industry analyst firm Forrester categorizes the SASE model as “Zero Trust Edge,” or ZTE).
But not all organizations have a cohesive approach across IT, network security, and networking teams. Therefore, they may prioritize security service edge (SSE) — a subset of SASE functionality primarily focused on securing access to the web, cloud services, and private applications.
Additionally, while most SASE platforms include the core capabilities noted earlier, some include additional SSE capabilities, such as:
- Remote browser isolation (RBI): RBI applies the Zero Trust principle to web browsing by assuming no website code (e.g. HTML, CSS, JavaScript) should be trusted to run by default. RBI loads webpages and executes any associated code in the cloud — away from users’ local devices. This separation helps prevent malware downloads, minimizes the risk of zero-day browser vulnerabilities, and defends against other browser-borne threats
- Data loss prevention (DLP): To prevent data from being stolen or destroyed without permission, DLP technologies detect the presence of sensitive data in web, SaaS, and private applications. In combination with a SWG, DLP solutions can scan data in transit; in combination with a CASB, DLP solutions can scan data at rest.
- Digital experience monitoring (DEM): DEM is a tool for monitoring user behavior and their experiences with website traffic and app performance. DEM helps organizations capture real-time data around network issues, performance slow-downs, and application outages. This helps to pinpoint network issues and identify the root causes of connectivity anomalies
SSE is a common stepping stone to a full SASE deployment. However, some organizations (particularly those with mature SD-WAN deployments) may not be looking to fully consolidate to a single SASE vendor. Those organizations can deploy individual SASE components to address their immediate use cases, with the option to expand their platform consolidation efforts over time.
How Cloudflare enables SASE
Cloudflare One is Cloudflare’s SASE platform for securing enterprise applications, users, devices, and networks. It is built on Cloudflare’s connectivity cloud - a unified, composable platform of programmable cloud-native services that enable any-to-any connectivity between all networks (enterprise and Internet), cloud environments, applications and users.
Cloudflare One services (which includes all the aspects of SASE) are designed to run across all Cloudflare network locations, so all traffic is connected, inspected, and filtered close to the source for the best performance and consistent user experience. Learn more about Cloudflare One.